Shipping Pre-registered Keys
This section describes how to work with shipments of pre-registered YubiKeys generated using the Yubico pre-registration service Yubico FIDO Pre-reg available through identity provider (IdP or IDP) integration.
About Yubico FIDO Pre-reg
The Yubico FIDO Pre-reg service reduces the IT administrative burden and improves end-user experience by standardizing and streamlining YubiKey onboarding and account recovery, helping organizations become phishing-resistant.
With Yubico FIDO Pre-reg, the IT administrator (IT admin) for an organization can use the YubiEnterprise API together with an identity provider’s WebAuthn API and automated workflows to order pre-registered YubiKeys for end users. The YubiKeys are pre-registered and shipped directly to the specific end user who receives a randomly generated PIN separately, and can immediately authenticate using their YubiKey.
FIDO Pre-reg Integrations
Yubico FIDO Pre-reg currently supports the following IdPs:
- Okta - see the Yubico FIDO Pre-reg with Okta Integration Guide.
- Microsoft Entra ID (Early Access) - see the Yubico FIDO Pre-reg with Microsoft Integration Guide.
Note
Currently you can only request one (1) YubiKey per shipment request using Yubico FIDO Pre-reg.
Managing Pre-reg Shipments
The following provides an overview of how to manage shipment requests for pre-registered YubiKeys.
Viewing Pre-reg Shipments
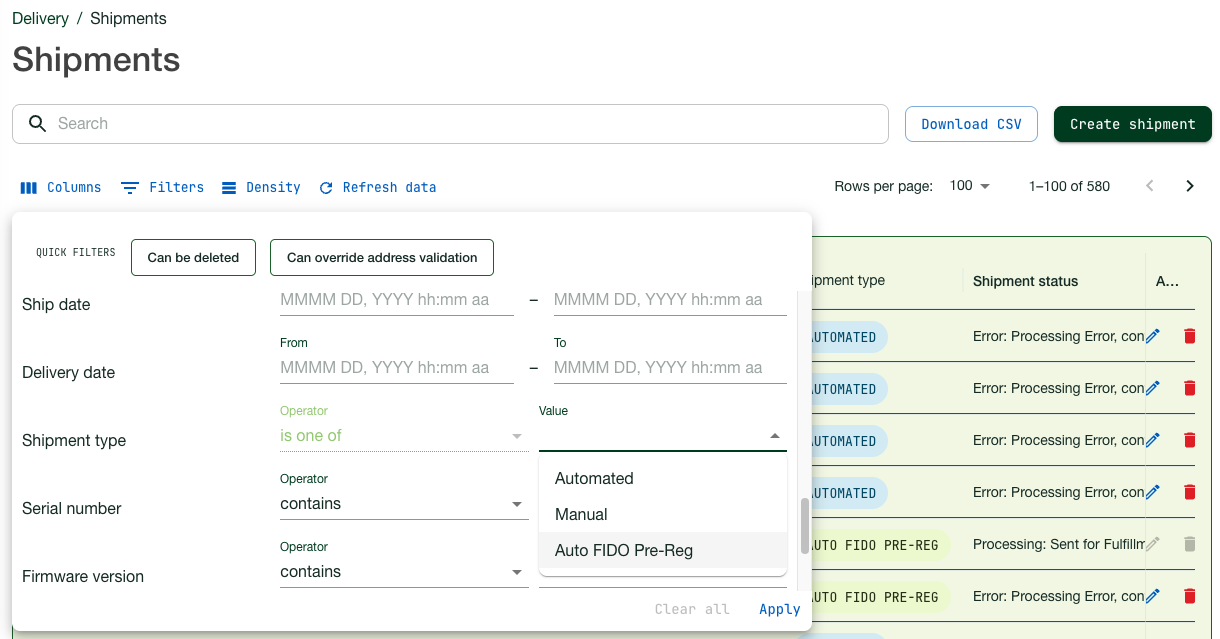
Just as for other types of shipment requests, you can monitor the status of pre-registered shipments for your organization in the Shipments page of the Customer Portal. Pre-registered shipments are indicated as AUTO FIDO PRE-REG in the Shipment type column on the page.
To locate a specific pre-registered shipment, do the following:
- Use the Filters function to filter out pre-registered shipments. Click Filters, select “Auto FIDO Pre-reg” as Shipment type, and click Apply.
- You can also use search in combination with filters to drill down further into the list of shipments. For more information, see Searching Shipments.
Editing Pre-reg Shipments
Just as for other types of shipments, you can update a pre-registered shipment from the Customer Portal until it is locked for processing and fulfillment. Shipments that can be edited are indicated with an Edit icon in the Shipment status column of the Shipments page.
You can update the recipient and address information, the delivery type, or you can delete the shipment request. Note that products included in a pre-registered shipment request cannot be modified. For more information, see Editing and Deleting Shipments.
Viewing Customization Information
A FIDO pre-registered YubiKey is considered a customization, and therefore Yubico provides a unique Customization ID required for the FIDO Pre-reg integration. To view your organization’s Customization ID, see Customizations.